
In today’s interconnected world, personal gadgets like smartphones, laptops, and tablets are integral to daily life. However, these devices are increasingly targeted by cyber threats aiming to steal data, compromise privacy, or disrupt functionality. Implementing robust cybersecurity measures is essential to safeguard personal information and maintain device integrity. This guide outlines 14 practical steps to enhance the security of personal gadgets against online threats.
Keep Software and Operating Systems Updated
Regularly updating device software and operating systems is crucial for security. Updates often include patches for known vulnerabilities that cybercriminals might exploit. Enabling automatic updates ensures devices receive the latest protections promptly. Neglecting updates can leave devices exposed to malware and other cyber threats.
Use Strong, Unique Passwords

Employing strong, unique passwords for each account significantly reduces the risk of unauthorized access. Passwords should be complex, combining letters, numbers, and symbols. Avoid reusing passwords across multiple platforms. Utilizing a reputable password manager can help manage and generate secure passwords effectively.
Enable Multi-Factor Authentication (MFA)
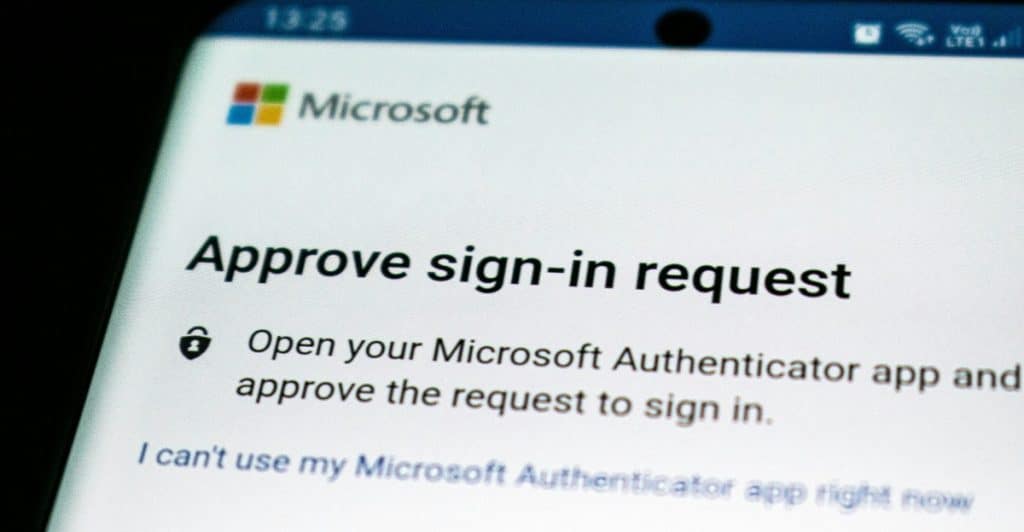
MFA adds an extra layer of security by requiring additional verification beyond just a password. This could be a code sent to a mobile device or a fingerprint scan. Implementing MFA makes it more challenging for unauthorized individuals to access accounts, even if passwords are compromised.
Be Cautious with Public Wi-Fi Networks
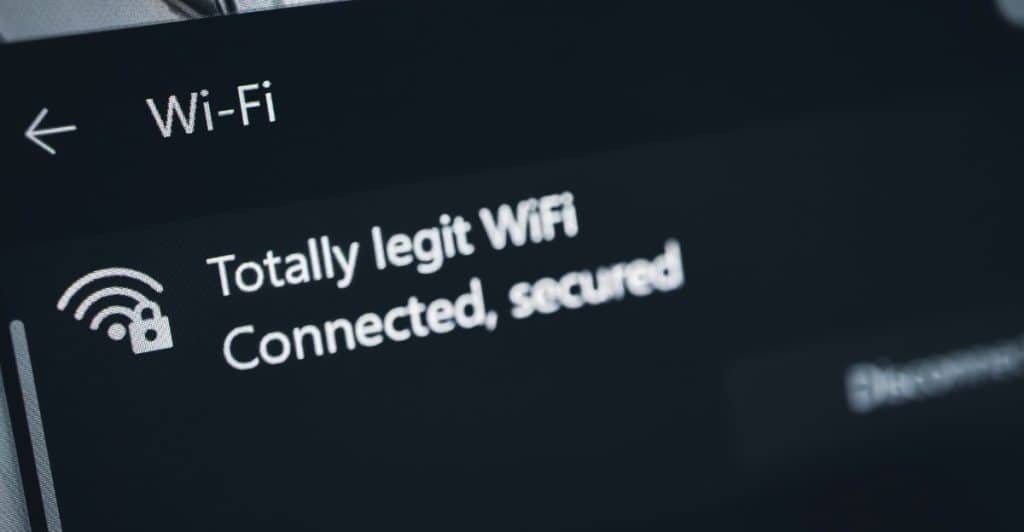
Public Wi-Fi networks are often unsecured, making them hotspots for cybercriminal activity. Avoid accessing sensitive information or conducting financial transactions over public Wi-Fi. If necessary, use a Virtual Private Network (VPN) to encrypt the connection and protect data from potential eavesdroppers.
Install Reputable Security Software

Installing trusted antivirus and anti-malware software provides a defense against various cyber threats. These programs can detect and neutralize malicious software before it causes harm. Regularly updating security software ensures it can recognize and combat the latest threats effectively.
Regularly Back Up Data

Regular data backups protect against data loss due to cyberattacks like ransomware. Utilize both cloud-based and physical storage solutions to ensure data redundancy. Automating backups can help maintain up-to-date copies of important files without manual intervention.
Limit App Permissions

Review and manage the permissions granted to applications on devices. Some apps may request access to data or features they don’t need to function. Limiting permissions reduces the potential for data misuse or unauthorized access to personal information.
Secure Home Wi-Fi Networks

Protect home Wi-Fi networks with strong, unique passwords and encryption protocols like WPA3. Regularly updating router firmware can patch security vulnerabilities. Disabling remote management features and hiding the network SSID can further enhance security.
Be Wary of Phishing Attempts

Phishing attacks often come in the form of emails or messages that appear legitimate but aim to steal personal information. Avoid clicking on suspicious links or downloading attachments from unknown sources. Verify the authenticity of requests for sensitive information before responding.
Use Secure Browsers and Extensions
Opt for web browsers known for robust security features. Utilize extensions that block ads, trackers, and malicious websites. Regularly update browsers and extensions to protect against newly discovered vulnerabilities.
Disable Unused Features

Turn off features like Bluetooth, NFC, or location services when not in use. Disabling unused features reduces the attack surface available to cybercriminals. Regularly reviewing device settings can help identify and disable unnecessary functionalities.
Avoid Using Unknown USB Devices

Connecting unknown USB devices to personal gadgets can introduce malware. Avoid using USB drives from untrusted sources. If necessary, scan external devices with security software before accessing their contents.
Monitor Accounts and Devices Regularly

Regularly check accounts and devices for unusual activity. Set up alerts for unauthorized access attempts or changes to account settings. Promptly addressing suspicious activity can prevent potential security breaches.
Educate Yourself on Cybersecurity Best Practices

Staying informed about the latest cybersecurity threats and best practices is vital. Participate in training sessions or follow reputable sources for updates. An informed user is better equipped to recognize and respond to potential security issues.
Conclusion

Protecting personal gadgets from cyber threats requires a proactive and informed approach. By implementing these 14 strategies, individuals can significantly reduce the risk of cyberattacks and safeguard their personal information. Regularly reviewing and updating security measures ensures continued protection in an ever-evolving digital landscape.






Ask Me Anything